All Posts

Configuring Unifi to route network traffic via Proton VPN
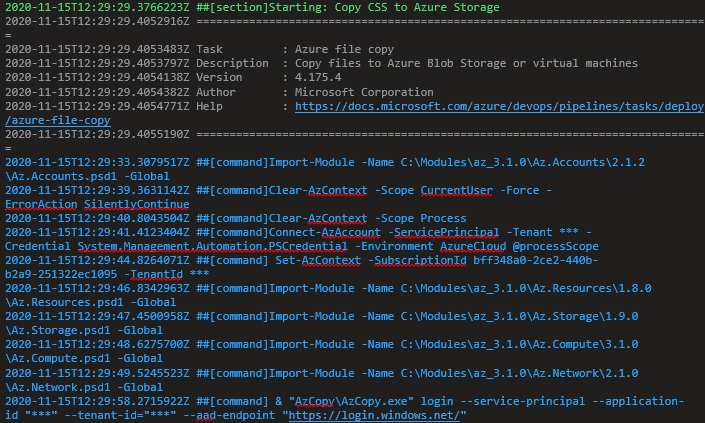
Solving the Azure Copy permissions by ensuring that the correct roles are applied to the service principal at the storage account IAM level.

Creating a NAS drive can be a simple affair however maintainability becomes an issue when you are beholden to specific OEMs. An alternative is to try and configure your server as much as possible using this method of a Pi and a SSD.

Configuring PiHole and Unifi for DNS content filtering

Using & configuring SonarCloud code analysis on a nodeJs project for static code anaylsis.

The library that I use across this site is called PrismJs it's an easy and clean JavaScript library for styling and highlighting code. It's simple to configure download and use, so I will

The security tools I use range from VPNs, encrypted emails and secure messaging. These tools facilitate different needs and allow me access different security protocols when necessary.

An example on how to use Polly's SDK to retry HTTP requests in .net. The Polly SDK has several policies which allow developers to express HTTP logic such as retries.

I have a reactjs component that uses the Intl.NumberFormat class

Reducing the amount of 3rd party scripts on your site is essential for performance and security reasons.

We are going to create 3 main rules which will prevent the IoT network from communicating with the main network, except to see the DNS server.

You'll also need to add some script tags on that same page which reference the react libraries & the script file that will contain all of the custom components created for the application

Azure functions are a great way to encapsulate core non sequential functionality that can be run in a background process

I recently migrated from .NET Core 2.0 to .NET Core 3.0 and here's the steps I had to take. Upgrade all project references from 2.0 -> 3.0
Below I will demonstrate how to setup a server running NodeJs that performs client certification authentication which will reject any requests not made with a valid certificate.
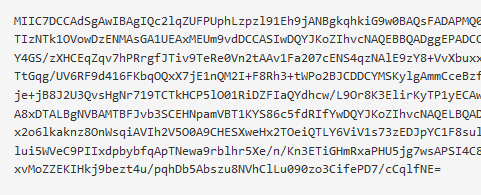
Below shows a code example of how to covert a certificate to a Base64 string in order to create a point to site VPN for use with Azure.

What does a company do when a security incident happens? How do they react? What is the process that they follow to resolve the issue and ensure that it doesn't happen again?
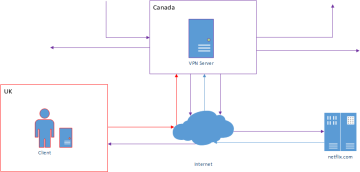
A VPN stands for virtual private network. It's purpose is to create a connection between your computer and another network securely, e.g. connecting to a work network.

This article will demonstrate how to force client certificate authentication using Internet Information Services 10. (This may be applicable to other versions of IIS.)
It's that time again. Now that Apple have released their truly wireless earbuds its time for a comparison of the what the market is currently offering.
Creating a NotFound / 404 rule within ASP.NET Core is quite simple, and once you've created that you'll be able to create custom error pages for all error status codes.
I am going to outline (as briefly as possible) how to ensure a Node application is restarted effectively if an uncaught exception is thrown, whether that exception is synchronous or asynch

Two factor authentication is a two step process which is used by websites to login users. There are many forms of two factor authentication, but for this blog I will focus on the process t
I've always contemplated about whether to get a solid state drive or by a new laptop. Finally I decided on both! The change in performance is incredible. I bought my new HDD from Crucial a
Ever though about moving all of your photos or maybe all of data out of Google? Google Takeout is the answer to your problems.
There are many features which come with Productivity Power Tools 2012 (aka free mini resharper), however one of my favourite features is the new solution wide Remove and Sort.
The key to this publish dilemma is Publish Profiles, Using these will change your life forever. These can be created manually but the easiest way is to use the publish wizard in Visual Stu
JQuery has a lot of plugins and add-ons which allow you to achieve some powerful customisations

OAuth 2.0 is a protocol (set of rules) which allows you to access a user's personal information without having to know their user credentials, i.e. username or password
I'm up and running now with Team Foundation Service, and I can say that I'm quite impressed. http://tfs.visualstudio.com/en-us/ I've set up a continuous integration environment at https://
In my experience as a developer I have observed various release processes that are used to get code to production
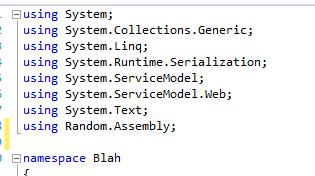
Have you ever seen a error like the one below: System.IO.FileNotFoundException: Could not load file or assembly 'Missing.Assembly.dll, Version=1.0.20.15800, Culture=neutral, PublicKeyToken
Bonjour Amigos, Just upgraded to Windows 8 Pro on the following machine: (Just look at the spec)
Using ADO.NET is a great way to connect to data provider that exists outside the .NET framework to connect to a database. There are many data providers out there, MySQL,PostgreSQL, FlySpee